The goal of a zero-trust framework is to prevent attacks by denying untrusted access to applications and data from anywhere. It does this by continuously verifying users, devices, and networks to limit the impact of a breach.
Achieving a zero-trust architecture is challenging; the most successful organizations do so through an iterative process. It starts with aligning security strategy to business goals and defining outcomes, then building everything together from the inside out.
Improved Security
The most obvious benefit of a zero trust framework is improved security. Zero trust is a shift from the traditional castle-and-moat cybersecurity model, in which anyone outside the network perimeter is suspicious, and everyone inside gets the benefit of implicit Trust. A more proactive and adaptive approach that verifies each user and device continuously and automatically.
This shift is driven by the digitization of businesses and the need for people to collaborate from anywhere on any device. The result is a sprawling distributed workplace ecosystem that demands a correlation of real-time security context across multiple systems and devices.
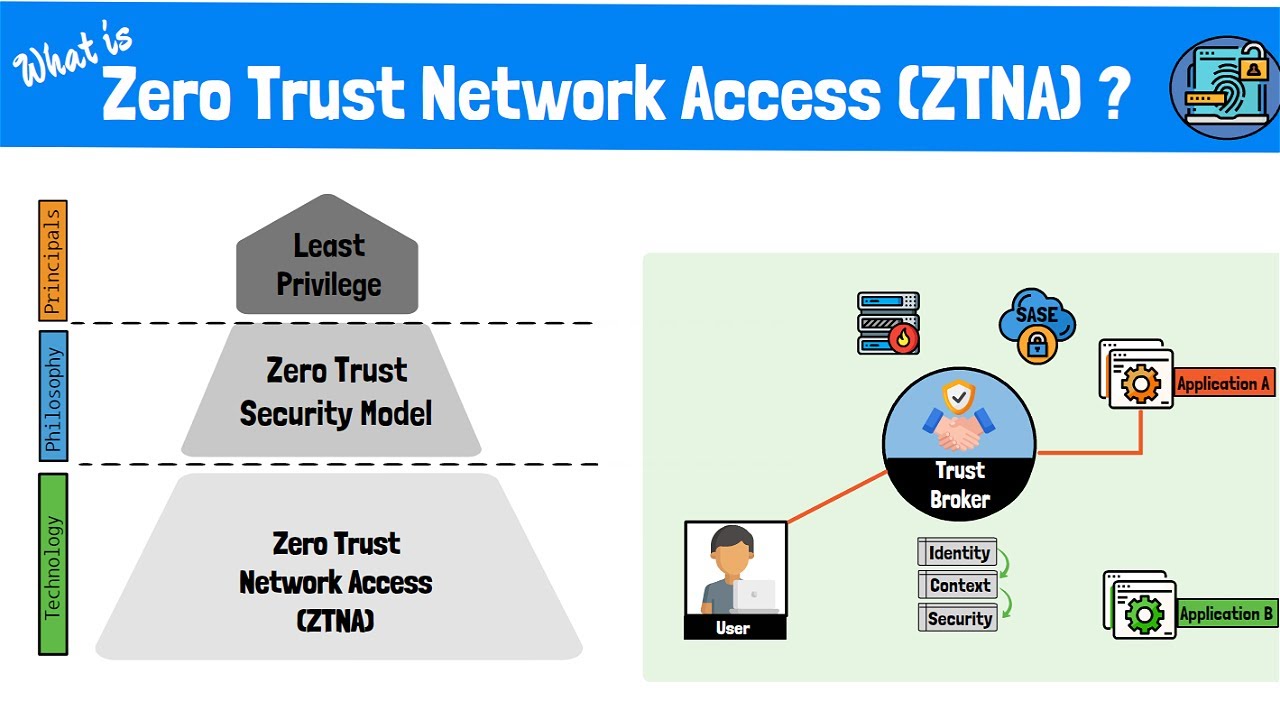
Zero trust approaches to access control begin with a deep understanding of the organization’s mission outcomes and how those must be achieved. From there, the architecture is built from the inside out to protect critical data/assets/applications and services (DAAS) and secure all paths to those assets.
Zero trust approaches also allow for micro-segmentation to limit an attacker’s ability to move laterally within the network. This can significantly reduce the damage if a breach occurs, help to contain it, and reduce the “blast radius” of attacks. Zero trust combines these security benefits with continuous visibility into users, devices, and applications and strong risk-coping capabilities to support a closed-loop security architecture. This helps to eliminate blind spots and improves the speed and accuracy of threat detection and response.
Enhanced Visibility
Zero Trust provides complete visibility of every device, user, and application accessing the network. By removing the assumption of Trust and authenticating each entity. This architecture allows you to identify assets and their locations, limit access, enforce policies, monitor for changes, and provide powerful alerts to prevent threats.
This framework uses micro-segmentation techniques and security measures, such as the Kipling method, to vet users, applications, and devices that seek access, ensuring the system knows who, what, where, when, and how they’re accessing. In addition, it enables data monitoring to watch for the presence of malicious software that could be infiltrating your systems and networks.
This security model eliminates the need for VPN, which often creates workflow chokepoints and slows down employees, dragging productivity. Moreover, it also reduces the risk of exposure to attacks that target remote workers. It limits the “blast radius” caused by a breach by ensuring that no one is granted standing privileges they shouldn’t have, whether from within or outside the organization. The continuous authentication and authorization of a zero-trust framework also make it easy to detect suspicious behavior that would be difficult for hackers to get around. This lets your security team quickly revoke access when the threat is detected.
Increased Flexibility
The zero trust model teaches us to “never trust, always verify.” This means every access request is treated as if coming from an open network. This is done by verifying identity, device context, and application data. It also involves applying micro-segmentation and least-privilege access controls to minimize lateral movement in the event of an attack. Zero Trust also uses rich intelligence and monitoring to flag real-time behavior anomalies.
As a result, implementing zero trust is a significant change to how your organization manages its security infrastructure. It takes a lot of work to get up and running. But once it’s implemented, it will provide substantial benefits.
This includes reducing the risk your company faces from phishing attacks and malware-driven user credentials. Compromised systems that enable attackers to gain widespread access. Zero Trust also makes it easier to secure remote users and the proliferation of mobile devices used for business.
Finally, zero trust can make it easier for your organization to quickly onboard third parties, contractors, and new employees. This is achieved through strong authentication, verification of the device and its operating system, and application-based authorization based on business processes. It also helps reduce risks associated with over-privileged service accounts by ensuring they have only the access needed to perform their jobs.
Reduced Risk
The zero-trust framework provides a strong defense against attacks by putting identity at the center of security. Zero Trust ensures that every movement in or out of data is verified and stops attackers before they reach confidential information. It also reduces the reliance on traditional endpoint protection solutions that fail to identify the attacker or stop lateral movement.
It provides continuous access verification based on all available information, including device, user, location, application, service, and workloads. This allows the organization to assume a breach and limit the “blast radius” of potential damage if a threat does infiltrate systems.
Segmenting applications and data into smaller granular segments is another key component of the zero-trust model. This can be done down to the workload level and prevents attackers from using accounts on devices or servers to travel laterally around the network.
Adopting a zero trust model is a multi-phase process that requires investment in infrastructure, resources, and time. But, when it is implemented correctly, a zero trust strategy can provide a powerful defense against threats. It meets regulatory compliance requirements like GDPR, CCPA, and HIPAA. An MSP can assess your security position, map out a roadmap to Zero Trust and help you implement and maintain the infrastructure required to achieve this advanced level of protection.